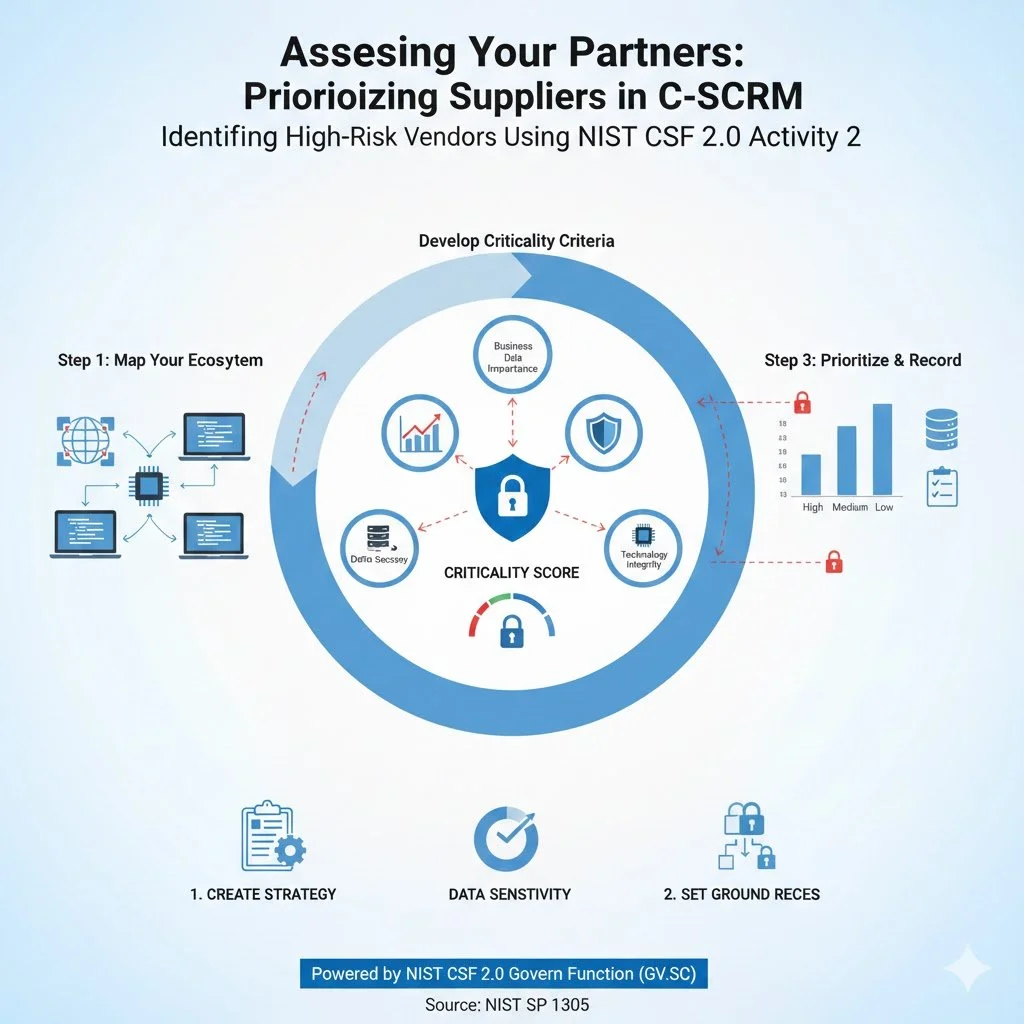
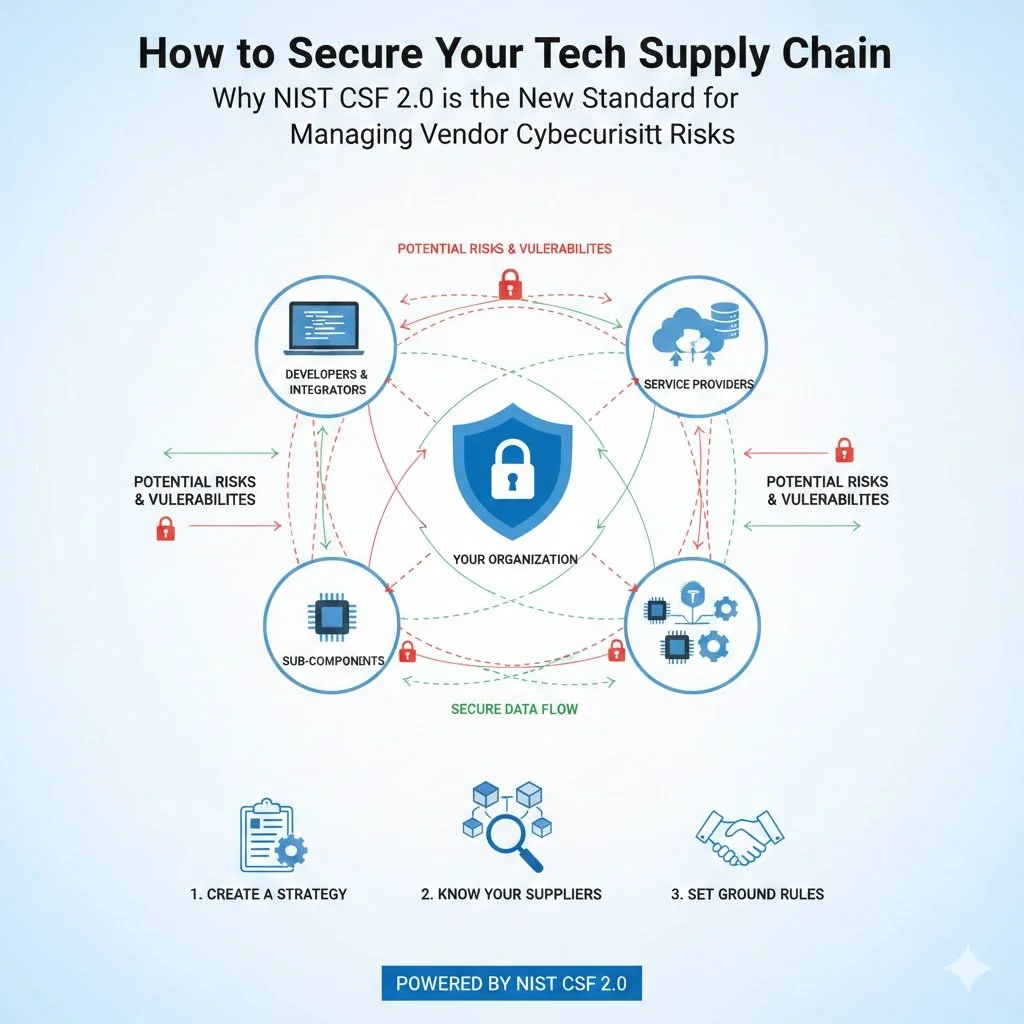
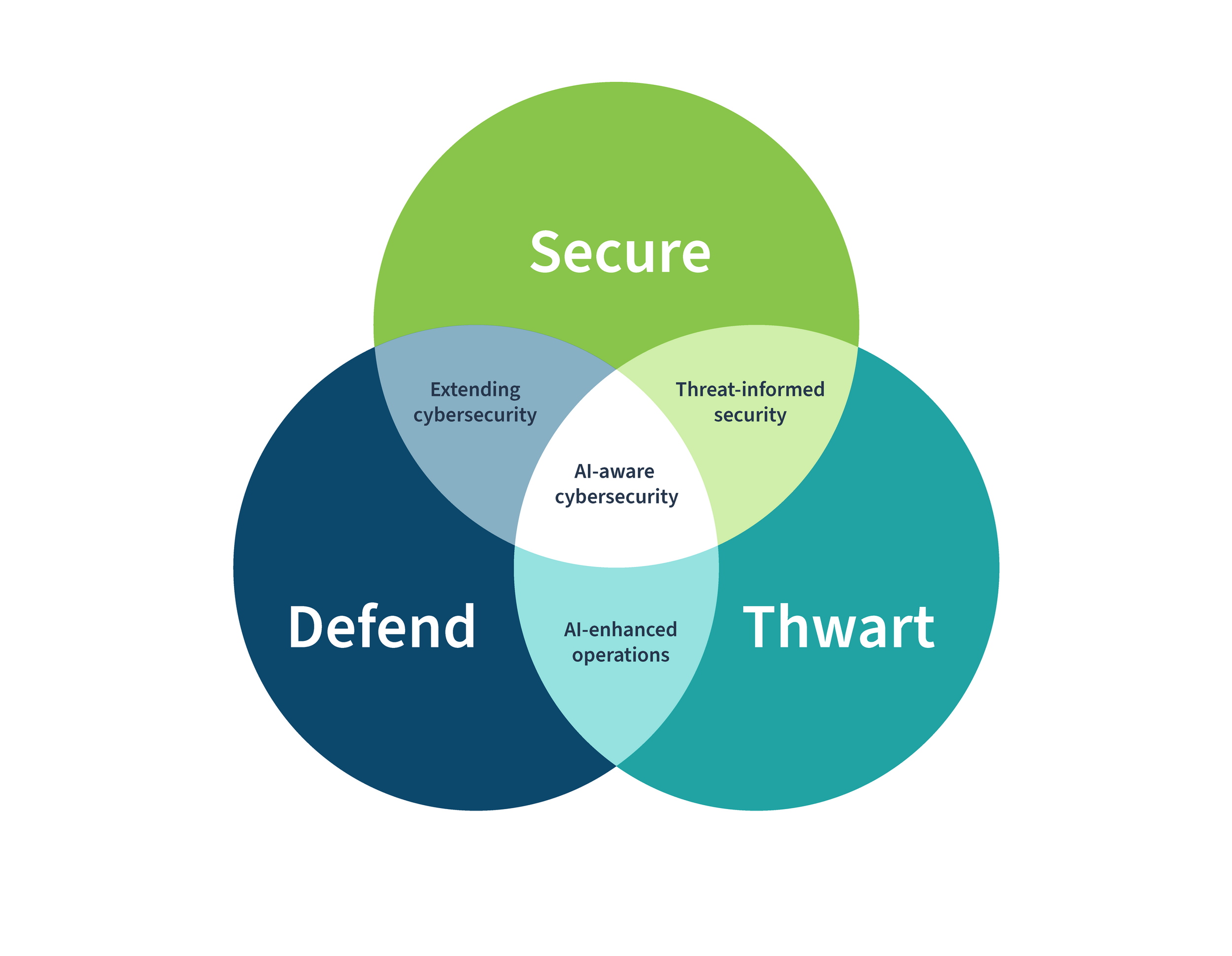
Many small business owners still view regulatory compliance as something reserved for large enterprises with deep pockets and full-time legal departments. This assumption is dangerously outdated. As we navigate 2025, regulatory scrutiny has extended its reach—and small businesses are firmly on the radar.
The landscape of compliance is evolving quickly. With rising cyber threats and increasing expectations around data privacy, regulators are tightening the rules and expanding their oversight. For small businesses, that means one thing: adapt or face the consequences.